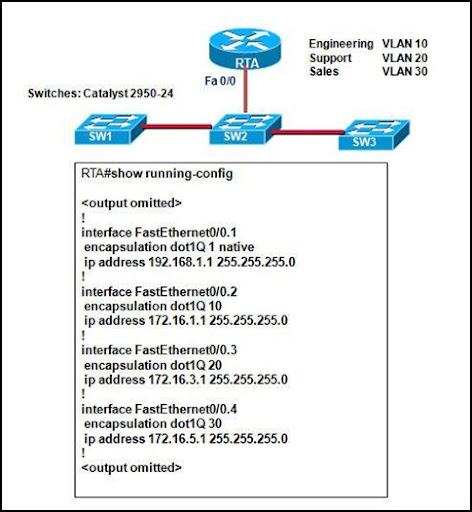
Refer to the exhibit. Based on the output shown, to which IP network should the workstations in the Support department belong?
• 192.168.1.0
• 172.16.1.0
• 172.16.3.0
• 172.16.5.0
Blog Ini berisi tentang ilmu komputer, Jaringan Komputer, Jawaban Cisco CCNA, Free Software, Dan masih banyak lagi yang tentunya itu semua Gratisss!!

to identify missing segments at the destination | |
to reassemble the segments at the remote location | |
to specify the order in which the segments travel from source to destination | |
to limit the number of segments that can be sent out of an interface at one time | |
to determine if the packet changed during transit |


